
On December 30, 2015, the U.S. Department of Defense (DOD) published a three-page interim rule to the Defense Federal Acquisition Regulation Supplement (DFARS) that gives government contractors a deadline of December 31, 2017 to implement the requirements of the National Institute of Standards and Technology’s (NIST) Special Publication (SP) 800-171.
These requirements protect the confidentiality of Controlled Unclassified Information (CUI) in non-federal systems and organizations. If you are a government contractor, failure to meet these requirements will result in the loss of your contracts.
The federal government is placing an ever-increasing emphasis on addressing cyber security threats. Any organization doing business with the federal government should expect these types of requirements to continue to evolve and intensify.
What is NIST?
The National Institute of Standards and Technology, a non-regulatory government agency that develops technology, metrics, and standards to drive innovation and economic competitiveness at U.S.-based organizations in the science and technology industry. As part of this effort, NIST produces standards and guidelines to help federal agencies meet the requirements of the Federal Information Security Management Act (FISMA). NIST also assists those agencies in protecting their information and information systems through cost-effective programs.
Why follow NIST Compliance for your Business?
We all know that cyber risks are not going away, truth is they’re creating more negative impacts to organizations. Cyber criminals have created an industry and are making lots of money attacking sensitive documentation. To prevent costly cyber-attacks, we turn to NIST. NIST has created a basic Cybersecurity framework (Version 1.1):
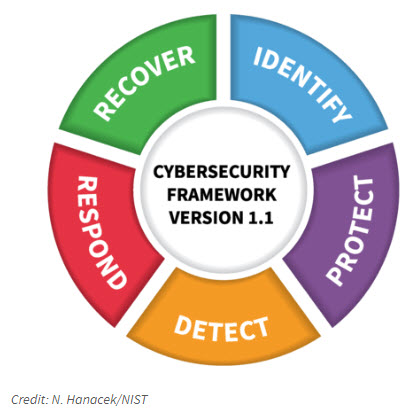
Important key points to understand with NIST:
- It’s not above and beyond what you should be doing – it’s framework demonstrates best Cybersecurity practices.
- It requires you to define and follow all of your security processes in one place
- Keep track of who is doing what on which machines (who is accessing data or granting access)
- Its much more than just installing the correct software. It covers everything from your infrastructure to your personnel, to your physical environment.
- Continuously monitor your security controls
- Understand your risk assessment
The 5 Core Functions
When considered together, the 5 Core Functions provide a strategic view of the lifecycle of an organization’s Cybersecurity risk management and should be treated as a key reference point. Here are the 5 Functions and how to comply with them:
1. Identify
Organizations must develop an understanding of their environment to manage Cybersecurity risk to systems, assets, data and capabilities. To comply with this Function, it is essential to have full visibility into your digital and physical assets and their interconnections, defined roles and responsibilities, understand your current risks and exposure and put policies and procedures into place to manage those risks.
2. Protect
Organizations must develop and implement the appropriate safeguards to limit or contain the impact of a potential Cybersecurity event. To comply, your organization must control access to digital and physical assets, provide awareness education and training, put processes into place to secure data, maintain baselines of network configuration and operations to repair system components in a timely manner and deploy protective technology to ensure cyber resilience.
3. Detect
Organizations must implement the appropriate measures to quickly identify Cybersecurity events. The adoption of continuous monitoring solutions that detect anomalous activity and other threats to operational continuity is required to comply with this function. Your organization must have visibility into its networks to anticipate a cyber incident and have all information at hand to respond to one. Continuous monitoring and threat hunting are very effective ways to analyze and prevent cyber incidents in ICS networks.
4. Respond
Should a cyber incident occur, organizations must have the ability to contain the impact. To comply, your organization must craft a response plan, define communication lines among the appropriate parties, collect and analyze information about the event, perform all required activities to eradicate the incident and incorporate lessons learned into revised response strategies.
5. Recover
Organizations must develop and implement effective activities to restore any capabilities or services that were impaired due to a cybersecurity event. Your organization must have a recovery plan in place, be able to coordinate restoration activities with external parties and incorporate lessons learned into your updated recovery strategy. Defining a prioritized list of action points which can be used to undertake recovery activity is critical for a timely recovery.
If you would like more information on NIST protocol / Cybersecurity or are interested in a compliance assessment for your business, please use the form below to reach out to our team.

