
Overwhelmed by vulnerabilities? SecurityRI.com provides a thorough Vulnerability Assessment Management Solution that accurately prioritizes risk, so you can take action on your most exposed assets.
Vulnerability Management / Vulnerability Assessment
A vulnerability scan (or even a vulnerability assessment) looks for known vulnerabilities in your systems and reports potential exposures.
Vulnerability scanning is a necessary part of maintaining your information security. For example, every new piece of equipment that is deployed should have a vulnerability scan run against it and another approximately monthly thereafter. Baseline reports on key equipment should be maintained, and changes in open ports or added services should be investigated. Vulnerability scanning can be used as a detective tool to alert an information security program when unauthorized changes have been made to the environment.
Network Vulnerability Scans
Obtaining and deploying a network vulnerability scanner is often the first step in creating a more proactive security program. To face modern attackers, it’s no longer enough to build high walls and wait out a siege; modern security programs must identify the holes that they could exploit and seal them up before the bad actors can take advantage. Network vulnerability scanners let you quickly assess your network for these holes, show you how to prioritize and remediate flaws, and provide a great barometer for the overall success and progress of your security team.
- Know What’s on Your Network
- Fix What Matters Most
- Bring Vulnerability Management to your Organization
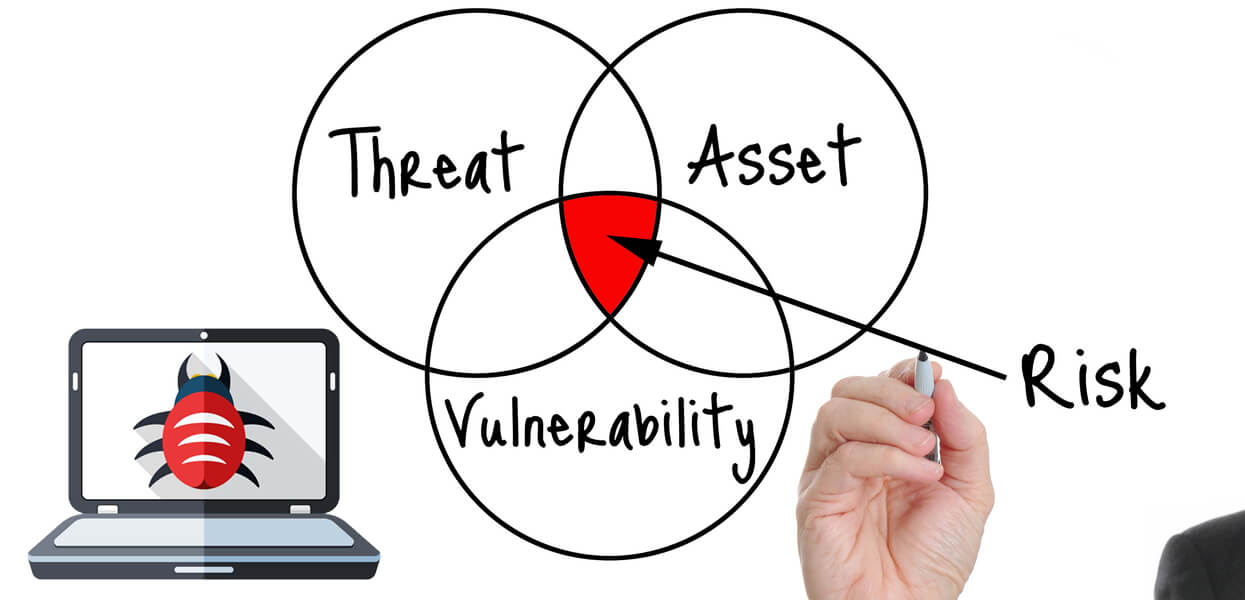
Vulnerability vs. Penetration Testing
Vulnerability scanning cannot replace the importance of penetration testing, and penetration testing on its own cannot secure the entire network.
Both are important at their respective levels, needed in cyber risk analysis, and are required by standards such as PCI, HIPAA, ISO 27001 etc.
Penetration testing exploits vulnerabilities in your system architecture while vulnerability scanning (or assessment) checks for known vulnerabilities and generates a report on risk exposure.
Both penetration testing and vulnerability scanning depend mostly on three factors: Scope, Risk and Criticality of assets and Cost and Time.
Penetration testing scope is targeted, and there is always a human factor involved. There is no such thing as automated penetration testing. It requires the use of tools, sometimes a lot, but it also requires an extremely experienced person to conduct the testing

