Security Strategy for Facility and Assets: A Holistic Approach
Security is a critical issue for businesses, organizations, and facility occupants alike. When it comes to creating a security strategy, there is no one-size-fits-all solution.
Each building has unique occupants and challenges, so the most effective security implementations are adapted and personalized to the needs of the building, occupant, and organization. What’s more, by taking a holistic approach to security and thinking about how it can integrate with existing building solutions, security teams are better equipped to mitigate and manage incidents and emergency events within their facility.
In this blog post, we will explore some of the key considerations when developing a holistic security strategy for your facility.
Developing a Security Strategy
One of the first things to consider when developing a security strategy is the layout of your facility. This includes factors such as the number of entrances and exits, the location of critical assets, and the flow of traffic throughout the building. By understanding how people move through your facility, you can more effectively deploy security resources and create checkpoints that will assist with protecting the facility.
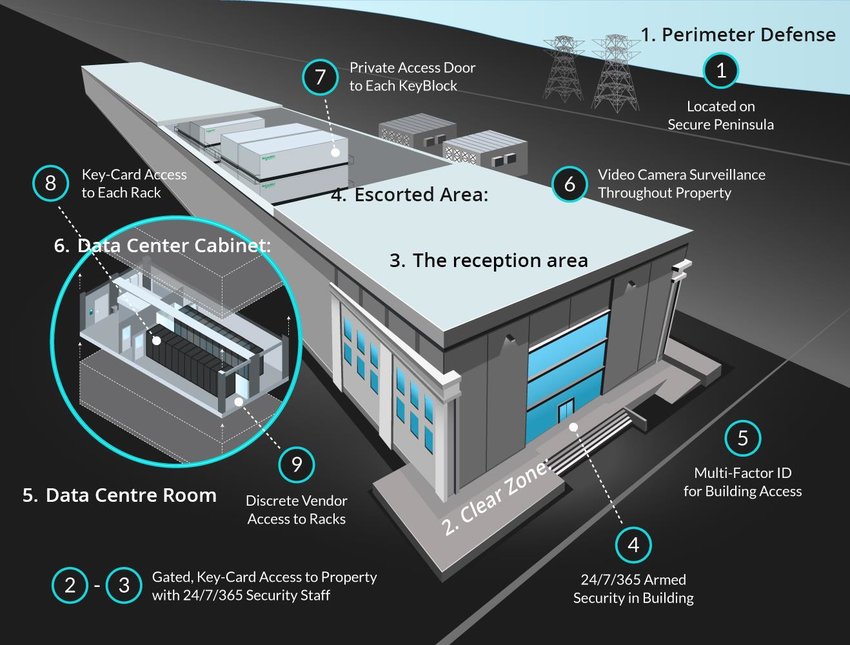
Where to begin?
- Build a blueprint – Making changes to your security without a plan can lead to problems. You need to map out the whole security infrastructure before you make any changes. This will help you design a better plan and also make it easier to integrate the new changes with the previous system.
Your blueprint should cover the following:
– Building perimeters
– Physical entry controls
– External, internal and environmental threat protection
– Power and telecommunications protocol
– Data protection
– Surveillance systems
– Physical security officers
– Reporting/escalation process
– Crisis management/plan - Integrate systems – Integrated design means that different systems or physical people work together. This makes it easier for the security team and protecting people, places, and assets. For example, if you have a security system with cameras, you can also have an AI camera with the smarts built in. Artificial intelligence will integrate with the physical security solution. The intelligence will assist the physical security officer when he cannot be at all places throughout the day/night. Alerts are configured and sent to the security team when abnormal activity occurs. This way, you have a scaled security solution – covering blind spots.
- Communication – Implement how you would like reporting escalated. Who are the key leaders that need to receive incident reports, surveillance footage, and/or daily activity information? How is this information being stored and escalated to law enforcement in the cause of an emergency?
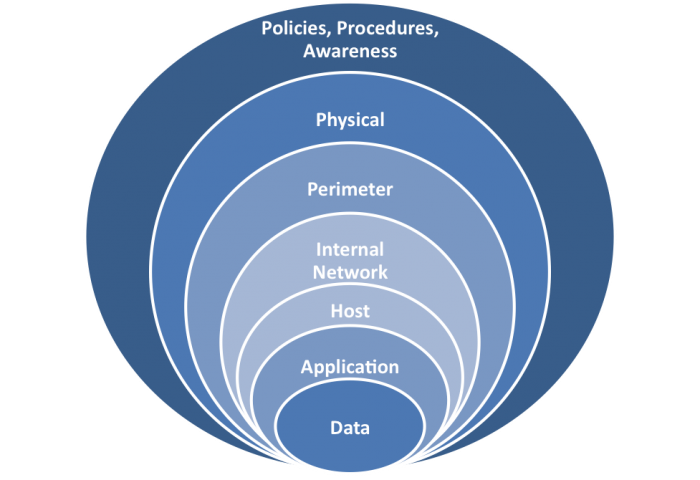
Business and security leaders should ensure that a consistent physical security program is developed and implemented across the company. Organizations that do not establish a comprehensive physical security program may overlook an important security function or leave an exposed physical vulnerability unaddressed. Organize all organizational stakeholders to create a thorough physical security plan supported by all management levels.
If you have any questions or need assist with your security strategy, please contact us below.





