Protect Your Business: The Top Benefits of Hiring Security Guard Companies in Rhode Island
The Importance of Business Security
As a business owner, ensuring the safety and security of your establishment should be a top priority. This is especially true in today’s world, where the threat of crime is ever-present. Protecting your business not only safeguards your assets and investments, but it also ensures the well-being of your employees and customers. One effective way to enhance your business security is by hiring professional security guard companies in Rhode Island.
Why Hiring Security Guard Companies is Essential
Hiring security guard companies is essential for several reasons. Firstly, these companies provide trained and experienced security personnel who are well-versed in handling various security situations. They are equipped with the knowledge and skills to detect and prevent potential threats, such as theft, vandalism, and trespassing. By having security guards present at your business premises, you create a visible deterrent for criminals and send a strong message that your establishment is not an easy target.
Moreover, security guard companies offer a sense of reassurance for your employees and customers. Knowing that there are security professionals on-site to handle any issues – provides peace of mind and promotes a safe working and shopping environment. This, in turn, can enhance employee productivity and customer satisfaction, leading to the overall success of your business.
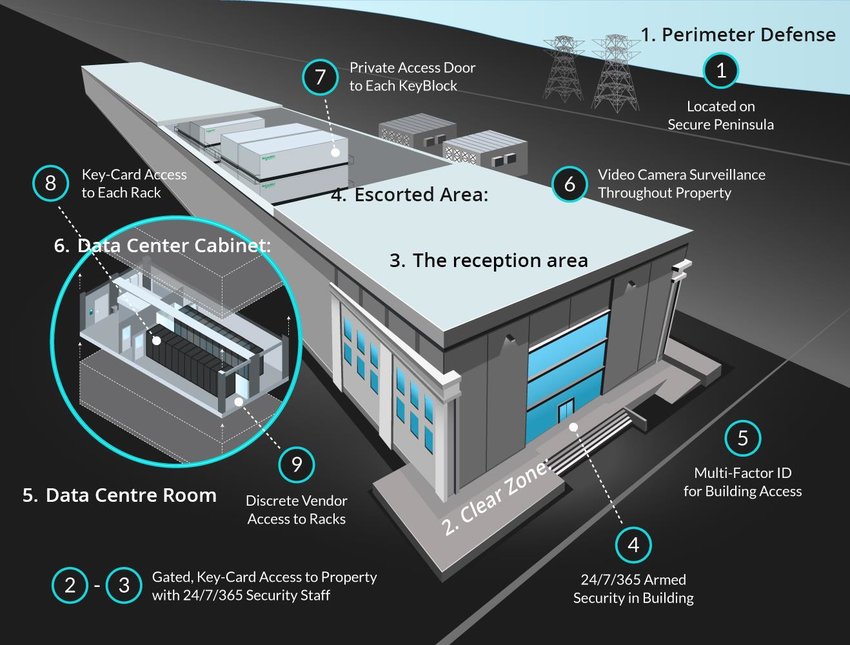
Benefits of Hiring Security Guard Companies in Rhode Island, such as SecurityRI
When it comes to hiring security guard companies in Rhode Island, one name that stands out is SecurityRI. Licensed number 1 in Rhode Island with 40+ years experience, SecurityRI offers a wide range of benefits that can greatly enhance your business security.
1. Professionalism and Expertise of Security Guard Companies
SecurityRI takes pride in providing highly professional and well-trained security personnel. The guards undergo on-the-job training to ensure they are equipped with the necessary skills to handle any security situation. Each location has different needs, therefore supervision will learn a location first then thoroughly train the scheduled security guards. With a team of experienced security guards by your side, you can trust that your business is in capable hands.
2. Deterrence of Crime
One of the primary benefits of hiring security guard companies like SecurityRI is the deterrence of crime. The presence of uniformed security guards alone can significantly reduce the likelihood of criminal activity on your premises. Criminals are less likely to target a business that has visible security measures in place, as it increases the chances of getting caught. By deterring crime, you protect your business from potential losses and maintain a safe environment for your employees and customers.
3. Round-the-Clock Protection
SecurityRI understands that security threats can arise at any time, day or night. That’s why they offer round-the-clock protection for your business. Whether it’s during regular business hours or after closing time, their security guards are available to provide constant surveillance and protection. This ensures that your business remains secure, even during non-operational hours when the risk of break-ins and vandalism is higher.
4. Handling Emergency Situations
In the unfortunate event of an emergency, having trained security guards on-site can make a significant difference. SecurityRI’s security guards are trained to escalate emergency situations immediately, including medical emergencies, fires, and natural disasters. They are equipped with the tools to respond swiftly and appropriately, ensuring the safety of everyone on your premises. The quick response can help avoid or minimize damages.
5. Customized Security Solutions
Every business has unique security needs, and SecurityRI understands this. SecurityRI offers customized security solutions tailored to your specific requirements. Whether you need security guards for access control, construction sites, or surveillance, SecurityRI can provide a comprehensive security plan that meets your business needs. Their flexibility and ability to adapt to changing circumstances make them a reliable partner in protecting your business.
Factors to Consider When Hiring Security Guard Companies in Rhode Island
When choosing a security guard company in Rhode Island, there are several factors to consider to ensure you make the right choice.
Firstly, it is essential to check the licensure and certifications of the security guard company. Ensure that they comply with all state regulations and have the necessary permits to operate in Rhode Island.
Secondly, evaluate the reputation and track record of the security guard company. Look for reviews and testimonials from other businesses they have served. A reputable company will have positive feedback and a proven track record of delivering excellent security services.
Additionally, consider the level of experience of the security guard company. Inquire about their management team, processes, reporting and tools. It is crucial to hire security guards who have the correct resources for your business location.
Conclusion
Protecting your business is of utmost importance, and hiring security guard companies in Rhode Island can provide numerous benefits. Companies like SecurityRI offer professionalism, expertise, and round-the-clock protection, ensuring the safety and security of your establishment. Our ability to handle emergencies and provide customized security solutions makes us a valuable asset to any business. When hiring a security guard company, consider factors such as licensure, reputation, training, and cost to make an informed decision.
Contact SecurityRI for a Free Security Assessment and take the first step towards enhancing the security of your business.